重点:
单单的防还是不能解决问题,下面是我们找出真凶了
给大家介绍一个工具可以像MMC计算机管理管理单元中的“会话”文件夹,显示的是通过网络登录到计算机的会话,
远程服务管理单元显示的是远程桌面登录的会话,但没有一个工具可以显示所有登录会话---不管任何登录类型--以及这些用户使用的程序列表。
这个工具是Sysinternals(现在已经是微软)的LogoSessions工具!
http://www.microsoft.com/technet/sysinternals/security/logonsessions.mspx
可以从这个地址去下载 Free
可以把LogoSessions中显示代码和其它工具显示的信息关联起来。
复制代码代码如下:
日志
=========
Logonsesions v1.1
Copyright (C) 2004 Bryce Cogswell and Mark Russinovich
Sysinternals - wwww.sysinternals.com
[0] Logon session 00000000:000003e7:
User name: WORKGROUPSDAHFPWE
Auth package: NTLM
Logon type: (none)
Session: 0
Sid: S-1-5-18
Logon time: 2008-2-18 15:33:05
Logon server:
DNS Domain:
UPN:
356: SystemRootSystem32smss.exe
404: ??C:WINDOWSsystem32csrss.exe
428: ??C:WINDOWSsystem32winlogon.exe
472: C:WINDOWSsystem32services.exe
484: C:WINDOWSsystem32lsass.exe
692: C:WINDOWSsystem32svchost.exe
836: C:WINDOWSSystem32svchost.exe
960: C:WINDOWSsystem32spoolsv.exe
1128: C:Program FilesSymantecpcAnywhereawhost32.exe
1164: C:WINDOWSSystem32svchost.exe
1300: C:Program FilesMcAfeeCommon FrameworkFrameworkService.exe
1376: C:Program FilesMcAfeeVirusScan Enterprisevstskmgr.exe
1452: C:Program FilesMcAfeeCommon FrameworknaPrdMgr.exe
1532: C:Program FilesRhinoSoft.comServ-UServUDaemon.exe
1696: C:WINDOWSSystem32svchost.exe
1912: C:WINDOWSSystem32svchost.exe
3844: C:WINDOWSsystem32wbemwmiprvse.exe
4000: C:WINDOWSsystem32dllhost.exe
3172: C:Program FilesMcAfeeVirusScan Enterprisemcshield.exe
3960: ??C:WINDOWSsystem32csrss.exe
396: ??C:WINDOWSsystem32winlogon.exe
372: C:WINDOWSsystem32inetsrvinetinfo.exe
2920: C:WINDOWSSystem32svchost.exe
2780: ??C:WINDOWSsystem32csrss.exe
1576: ??C:WINDOWSsystem32winlogon.exe
[1] Logon session 00000000:000081e5:
User name:
Auth package: NTLM
Logon type: (none)
Session: 0
Sid: (none)
Logon time: 2008-2-18 15:33:05
Logon server:
DNS Domain:
UPN:
[2] Logon session 00000000:0000c0f7:
User name: NT AUTHORITYANONYMOUS LOGON
Auth package: NTLM
Logon type: Network
Session: 0
Sid: S-1-5-7
Logon time: 2008-2-18 15:33:08
Logon server:
DNS Domain:
UPN:
[3] Logon session 00000000:000003e5:
User name: NT AUTHORITYLOCAL SERVICE
Auth package: Negotiate
Logon type: Service
Session: 0
Sid: S-1-5-19
Logon time: 2008-2-18 15:33:09
Logon server:
DNS Domain:
UPN:
[4] Logon session 00000000:5cbf7d87:
User name: SDAHFPWE-WUYMBImaggie
Auth package: NTLM
Logon type: RemoteInteractive
Session: 2
Sid: S-1-5-21-1476199771-2381760486-1211474579-1009
Logon time: 2008-2-21 9:44:18
Logon server: SDAHFPWE-WUYMBI
DNS Domain:
UPN:
3164: C:WINDOWSsystem32rdpclip.exe
740: C:WINDOWSExplorer.EXE
3528: C:Program FilesMcAfeeVirusScan EnterpriseSHSTAT.EXE
392: C:WINDOWSsystem32ctfmon.exe
3952: C:WINDOWSsystem32mmc.exe
336: C:Program FilesRhinoSoft.comServ-UServUAdmin.exe
[5] Logon session 00000000:60d81435:
User name: SDAHFPWE-WUYMBIIUSR_SDAHFPWE-WUYMBI
Auth package: NTLM
Logon type: NetworkCleartext
Session: 0
Sid: S-1-5-21-1476199771-2381760486-1211474579-1015
Logon time: 2008-2-21 10:55:33
Logon server: SDAHFPWE-WUYMBI
DNS Domain:
UPN:
[6] Logon session 00000000:000003e4:
User name: NT AUTHORITYNETWORK SERVICE
Auth package: Negotiate
Logon type: Service
Session: 0
Sid: S-1-5-20
Logon time: 2008-2-18 15:33:06
Logon server:
DNS Domain:
UPN:
2496: c:windowssystem32inetsrvw3wp.exe
[7] Logon session 00000000:000309aa:
User name: SDAHFPWE-WUYMBIjooline2008sh
Auth package: NTLM
Logon type: RemoteInteractive
Session: 1
Sid: S-1-5-21-1476199771-2381760486-1211474579-500
Logon time: 2008-2-18 15:35:34
Logon server: SDAHFPWE-WUYMBI
DNS Domain:
UPN:
[8] Logon session 00000000:60f64f82:
User name: SDAHFPWE-WUYMBIjooline2008sh
Auth package: NTLM
Logon type: RemoteInteractive
Session: 3
Sid: S-1-5-21-1476199771-2381760486-1211474579-500
Logon time: 2008-2-21 11:06:47
Logon server: SDAHFPWE-WUYMBI
DNS Domain:
UPN:
1840: C:WINDOWSsystem32rdpclip.exe
3580: C:WINDOWSExplorer.EXE
2876: C:Program FilesMcAfeeVirusScan EnterpriseSHSTAT.EXE
888: C:Program FilesRhinoSoft.comServ-UServUTray.exe
3280: C:WINDOWSsystem32cmd.exe
376: C:WINDOWSsystem32conime.exe
1820: C:Program FilesMcAfeeVirusScan Enterprisemcconsol.exe
720: C:WINDOWSsystem32NOTEPAD.EXE
2320: E:logonsessions.exe
==============================
在安全日志事件中,可以把输出的登录会话ID和安全日志事件说明进行关联,查找登录事件和会话相关的事件。
这样很容易找到是怎么回事了....
【麦咖啡(mcafee) VSE 8.5 服务器防挂马心得】相关文章:
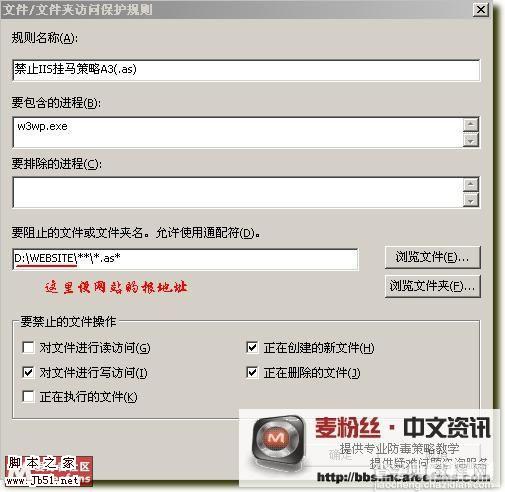
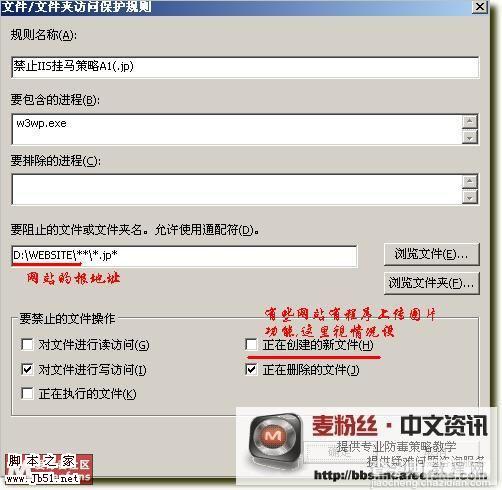
★ McAfee防止挂马 用McAfee阻止IIS写入asp文件
